Cambridge Technical Level 3 IT
0.0 / 5
- Created by: aboy
- Created on: 22-12-20 12:20
Input device
A device which is plugged in or connected to a computer
1 of 70
Output device
A signal which comes out from the computer
2 of 70
Central Processing Unit (CPU)
Unit that controls the actions of the Computer and manipulates required tasks
3 of 70
Motherboard
A circuit board that connects the CPU to the memory and the all other hardware.
4 of 70
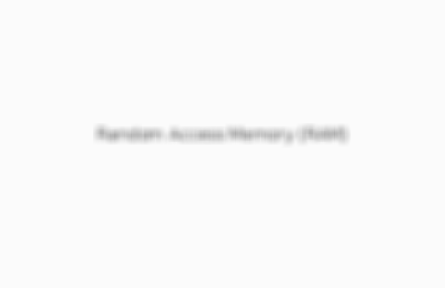
Random Access Memory (RAM)
RAM is volatile memory; the computer storage saved by the RAM is only maintained while the computer is powered.
5 of 70
Read Only Memory (ROM)
ROM is non-volatile memory; the computer will maintain instructions even when the computer is shut down.
6 of 70
Universal Serial Bus (USB)
Most common computer port
(Printer, Camera/camcorder, and mobile phone)
Digital communication of short distance
(Printer, Camera/camcorder, and mobile phone)
Digital communication of short distance
7 of 70
Firewire
Links devices which need high speed transfer of large amounts data
e.g. DVD player
e.g. DVD player
8 of 70
Serial Advanced Technology Attachement (SATA)
Connects optical and hard disk to computer
9 of 70
Ethernet port
Used for cable based networks which links directly to the computer's network card (NIC)
10 of 70
Hardware
The physical components of a computer
11 of 70
Software
A program that run on the computer which manages hardware
12 of 70
Solid State Drive (SSD)
internal computer storage device
Non-volatile memory
Fast read and write speed
no moving parts
Non-volatile memory
Fast read and write speed
no moving parts
13 of 70
Flash Memory
Low cost
Portable
No moving parts
Durable
e.g. USB and SD Card
Portable
No moving parts
Durable
e.g. USB and SD Card
14 of 70
Cloud Storage
Low cost
Easier management
Enables sharing and access from anywhere
Easier management
Enables sharing and access from anywhere
15 of 70
Copper wired connection
Twisted Pair (TP)
Commonly used in telephone systems
Several twisted pairs bought together to form a twisted cable
Untwisted pair (UTP)& Shielded Twisted pair
Commonly used in telephone systems
Several twisted pairs bought together to form a twisted cable
Untwisted pair (UTP)& Shielded Twisted pair
16 of 70
Fibre Optic Cables
The fastest delivery by a cable.
The thinner the cable the better the signal.
The signal is sent down a glass rod/core, as a beam of light ; Optical fibre lamp
The thinner the cable the better the signal.
The signal is sent down a glass rod/core, as a beam of light ; Optical fibre lamp
17 of 70
Coaxial Cable
Copper wire based connector. This wire can be used to link television set to an aerial socket (Sky TV)
18 of 70
Wireless connection
Do not use cable but use Radio Frequency (RF) to transmit data or instructions between devices
e.g. computer, printer, certain credit cards and payment terminals
e.g. computer, printer, certain credit cards and payment terminals
19 of 70
Wi-fi
Connecting devices via a network hub
Up to 92 meters depending on frequency and obstruction
Up to 92 meters depending on frequency and obstruction
20 of 70
Laser networks
Sending data using a light beam to devices in a line of sight.
e.g. Satellite communication
Up to 10km but can be blocked by fog or haze
e.g. Satellite communication
Up to 10km but can be blocked by fog or haze
21 of 70
Infarared technology
LED - emitting received by a photodiode in the receiving of a device
e.g. TV remote control
e.g. TV remote control
22 of 70
Microwave Communication
Short radio waves to send signals via microwave towers
Can provide analogue or digital format
Must be in a sight with no obstruction
Can provide analogue or digital format
Must be in a sight with no obstruction
23 of 70
Network Hub it
A node that broadcasts data to every computer or Ethernet-based device connect to it
24 of 70
Switch
A switch is a device in a computer network that connect other devices together.
Multiple data cables are plugged into a switch to enable communication between different networked devices.
Multiple data cables are plugged into a switch to enable communication between different networked devices.
25 of 70
Hybrid network
Any computer network that uses more than one type of connecting technology or topology
e.g. both Wi-fi and Ethernet cables to connect a computer router
e.g. both Wi-fi and Ethernet cables to connect a computer router
26 of 70
Router
Enables connection between network, switches to communicate between devices. To transfer data packets across the network.
27 of 70
Open Source Software
Software that is dedicated to a community who will provide help and support
free or very low cost
users can upgrade or change the software
may not have a user-friendly interface
free or very low cost
users can upgrade or change the software
may not have a user-friendly interface
28 of 70
Proprietary Software
Developed and professionally tested
There is a technical support platform (help service)
user licences apply
There is a technical support platform (help service)
user licences apply
29 of 70
Application software
Designed to carry out tasks
Account management, text creation and editing, presentation preparation and design drawing
Account management, text creation and editing, presentation preparation and design drawing
30 of 70
Utility Software
System software designed to help analyse, configure, optimise or maintain a computer
e.g. anti-virus software, backup software
e.g. anti-virus software, backup software
31 of 70
Protocols
A set of rules in which computers communicate with each other
32 of 70
HTTP(S)
Web transfer protocol
33 of 70
Transmission Control Protocol/Internet Protocol (TCP/IP)
The set of protocols used over the internet
It organises how packets are communicated and if they have the following source
It organises how packets are communicated and if they have the following source
34 of 70
Voiceover Internet Protocol (VoIP)
Method of digital telephone, video - conferencing and teleconferencing
Converts analogue sound to digital sound
Converts analogue sound to digital sound
35 of 70
Virtualisation
One physical computer performing the function of multiple computers
This is to create a simulated/ virtual network
This is to create a simulated/ virtual network
36 of 70
Hypervisor/Virtual Machine Monitor (VMM)
A piece of computer software, firmware or hardware
It creates and runs a virtual machine.
It creates and runs a virtual machine.
37 of 70
Servers
A server is a computer that provides data to other computers.
File server
Print server
Application & database Sever
Web, Mail and Hypervisor
File server
Print server
Application & database Sever
Web, Mail and Hypervisor
38 of 70
Computer Networks
The interconnection of computer to communicate and share files and resources
LAN - Local Area Network
WAN - Wide Area Network
CAN - Campus Area Network
MAN - Metropolitan Area Network
HAN - Home area Network
LAN - Local Area Network
WAN - Wide Area Network
CAN - Campus Area Network
MAN - Metropolitan Area Network
HAN - Home area Network
39 of 70
Network toplogies
Logical layout of devices connected to a network
Bus - Single main cable to which computers are connected to
Ring - All computers are connected in a circle
Star - All computers have their own link to a central computer
Mesh - Where each computer can
Bus - Single main cable to which computers are connected to
Ring - All computers are connected in a circle
Star - All computers have their own link to a central computer
Mesh - Where each computer can
40 of 70
Peer to Peer
Each computer is responsible for providing data. Each computer stores files and acts as a server.
E.g. Lime wire and Pirate Bay
E.g. Lime wire and Pirate Bay
41 of 70
Client Server
A relationship between two computers where the client makes a request to the server
e.g. Web Server - A web browser is the client which makes a request to the server and sends the website to the browser
e.g. Web Server - A web browser is the client which makes a request to the server and sends the website to the browser
42 of 70
Bandwidth
The amount of data that can be carried at once
Transmission speed - Measured in Mbps (Megabits per Second) or Gbps (Gigabits per Second)
Transmission speed - Measured in Mbps (Megabits per Second) or Gbps (Gigabits per Second)
43 of 70
Business system
Designed to connect all the organisations's intricate (complex) parts and interconnected steps to work together to achieve a business strategy
44 of 70
Management Information System (MIS)
The processing of information through computers and other intelligent device
45 of 70
Customer Relations Manager (CRM)
An approach to managing a company's interaction with current potential customers
46 of 70
Standard Operations Procedure (SOP)
A set of step-by-step instruction complied by an organisation to help carry out complex routine operations.
47 of 70
Help-desk
A resource intended to provide the customer or end user with information and support relating to products and services.
48 of 70
Ethics
A set of moral principles that governs a person's behavior or the conduction of an activity
49 of 70
Whistle-blowing
The practice of reporting abuses at work on a small or large scale for the hope of something being done about it
50 of 70
Discrimination
Disability/gender/sexuality discrimination - under the Equal opportunities act
51 of 70
Operational Issues
The issue that affects the daily or routine operations carried out by a business in order to fully function
52 of 70
Security Information
This is about making sure all information stored by a company is secure and where necessary backups have been made.
53 of 70
Backups
The use of backups & the restoration of the data are critical in ensuring the data is safe and secure.
54 of 70
Health and Safety
Governed by Health & Safety at Work Act 1974, employers are legally obliged to look after the safety of their customers and staff.
Eye - Strain
Back and Neck Ache
Repetitive Strain Injury
Eye - Strain
Back and Neck Ache
Repetitive Strain Injury
55 of 70
Procedures
The act of informing of staff of how to do things and polices are in place.
56 of 70
Regulations
This is the process of updating and informing staff of legal issues in their workplaces
57 of 70
Process
The act of making a company safe, wheelchair access, barriers, clothing, training on safety measures, fire tests, ladder climbing, object lifting. Procedures are practiced reviewed and improved regularly.
58 of 70
Disaster and Planning & Recovery
The process and procedure a company puts in place to ensure that essential functions can continue during and after a disaster
59 of 70
Phishing
An e-mail fraud method which the perpetrator sends out legitimate- looking email.
60 of 70
Hacking
The process by which a Hacker gains unauthorised access to a computer system or a network.
Hacking can be carried out for reason such as data theft and simply testing organisation security.
Hacking can be carried out for reason such as data theft and simply testing organisation security.
61 of 70
Virus
A computer program that is designed to replicating itself by copying itself into the other programs stored in a computer.
62 of 70
Trojan
• Trojans are stealth applications which are designed to allow others to access your system
63 of 70
Interception
This is where an unauthorised party gain access to an asset.
It is a direct threat to confidentiality and this can have major repercussions for a company e.g. poor image and reputation. to capture data on a network.
It is a direct threat to confidentiality and this can have major repercussions for a company e.g. poor image and reputation. to capture data on a network.
64 of 70
Eavesdropping
An electronic attack where digital communications are intercepted by an individual who they are not intended.
65 of 70
Data Theft
The theft of data that can be used for malicious purposes.
66 of 70
Social Engineering
The context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information.
67 of 70
Lock & Key
This is defined as 'when essential systems are held in rooms and buildings which are secured under lock and key'
You will see a slot at the side where a padlocked chain can be placed to secure a device.
You will see a slot at the side where a padlocked chain can be placed to secure a device.
68 of 70
Digital Keypads
These can be reprogrammed at regular intervals but cannot prevent access by observation or by colleagues passing the codes onto others.
69 of 70
Biometrics
The implementation of technology to use biological information about ourselves as a method of unique identification.
Rentinal Scan
Fingerprint Recognition
Voice Recognition
Rentinal Scan
Fingerprint Recognition
Voice Recognition
70 of 70
Other cards in this set
Card 2
Front
A signal which comes out from the computer
Back
Output device
Card 3
Front
Unit that controls the actions of the Computer and manipulates required tasks
Back

Card 4
Front
A circuit board that connects the CPU to the memory and the all other hardware.
Back

Card 5
Front
RAM is volatile memory; the computer storage saved by the RAM is only maintained while the computer is powered.
Back
Related discussions on The Student Room
- btec nationals diploma IT »
- Entry requirements with mixed courses »
- UCAS application What is my qualification called for OCR media »
- Health and social care alevel- whats my overall »
- Good universities without maths A-level “Urgent” »
- Uni of Manchester Appeal »
- Should I do 3 A levels instead of BTEC Computing National*Extended Diploma Level 3? »
- Should I do 3 A levels instead of BTEC Computing National*Extended Diploma Level 3? »
- Can I go to university for marketing with a btec in media »
- Business a level »
Similar ICT resources:
0.0 / 5
0.0 / 5
0.0 / 5
0.0 / 5
3.5 / 5 based on 2 ratings
Comments
No comments have yet been made