Computer Networks
5.0 / 5 based on 2 ratings
- Created by: ShackletonJ
- Created on: 27-04-18 11:59
LANs
LANs (Local Area Networks):
- covers a small geographical area located on a single site
- all the hardware is owned by the organisation that uses it
- they are either wired (e.g. with Ethernet cables) or wireless (using Wi-Fi)
- can connect to various devices (PCs, tablets, smart TVs and printers)
Why Use a LAN?
- they make sharing files easier - networks can access the same files, work collaboratively on them and copy files between machines
- they can share hardware (such as printers)
- the Internet connection can be shared between every device connected to the LAN
- software can be installed and updated all at once rather than one-by-one
- you can communicate with LAN users cheaply and easily (e.g. with instant messaging)
- user accounts can be stored centrally, so users can log-in from any device on the network
1 of 26
WANs
WANs (Wide Area Networks):
- a network that connects LANs in different geographical locations
- organisations must hire infrastructure (e.g. communication lines) from telecommunications companies, who own amd manage the WAN - this makes a WAN much more expensive than a LAN
- WANs may be connected using fibre or copper telephone lines, satellite links or radio links
- the Internet is one large WAN
2 of 26
Factors that can Affect the Performance of Network
- Bandwidth is the amount of data that can be transferred in a given time (e.g. 500Mbps)
- The greater the bandwidth, the better the network can perform
- Available bandwidth is shared bewteen the users of a network - so having too many users or heavy use (e.g. video streaming) may cause congestion and slow the network
- Bandwidth to individual users can be limited to try and prevent congestion
- Wired connections are generally faster and more reliable than wireless connections
- Fibre optic cables give much better performance than copper cables
- Wireless performance is dependent on signal quality - this can be affected by the range of the device, the amount of interference from other devices and physical obstructions like thick walls or buildings
- The choice of hardware (other than cables) and network topology can also have a large effect
3 of 26
Required Pieces of Hardware
NIC (Network Interface Card):
- internal hardware (built into the motherboard) that allows a device to connect to a network
- exist for both wired and wireless connections
Switches:
- connect devices on a LAN
- receive data (in units called frames) from one device and transmits this data to the device on the network with the correct MAC address (Media Access Control)
Routers:
- responsible for transmitting data between networks - they are always connected to at least two different networks
- on the Internet, they direct data (in units called packets) to their destination
- used in homes and offices to connect the LAN to the internet
4 of 26
Cables
Ethernet (CAT 5e and CAT 6):
- used to connect devices in a LAN
- 'twisted pair' cables, containg four pair of copper wires
- the pairs of copper wires are twisted together to reduce internal interference
Coaxial:
- also used to connect devices in a LAN (typically serial networks/ring topologies)
- single copper wire surrounded by a plastic layer of insulation and a metallic mesh
- the metallic mesh provides shielding from outside interference
Fibre-Optic:
- can be used to connect to switches in large LANs or to connect multiple LANs
- transmit data as pulses of light
- high performance (so high cost)
- do not suffer interference
- can transmit over large distances without loss of signal quality
5 of 26
Pieces of Hardware Required for Wireless Networks
- Wireless networks use radio waves to transmit data
- To set up a wireless network, a Wireless Access Point (WAP) device is required
- The WAP is a switch that allows devices to connect to the network wirelessly
- Hotspots are locations where you can connect to a WAP
- Devices need wireless capability to be able to connect to a wireless network
- Dongles can be used to connect devices that do not have the necessary hardware built in
- USB Dongles can be plugged into computers to allow them to connect wirelessly to the internet
- HDMI Dongles can be used to stream high-quality video to a TV (using wireless networks)
6 of 26
Wi-Fi Connections
- Wi-Fi uses 2 radio frequency bands - 2.4GHz and 5GHz
- The bands are split into numbered channels that each cover a small frequency range
- The channels in the 2.4GHz band overlap (there are 14 channels spaced 5MHz apart)
- Wi-FI performance is affected by interference between networks using adjacent channels - to avoid problems, only certain channels that are spaced apart tend to be used
- Data on Wi-Fi networks should be encrypted (the security protocols for this are WPA (Wi-FI Protected Access), WPA2 and WEP
Advantages of 2.4GHz Frequency Band:
- has a greater range - can serve devices across a greater area
- is better at getting through solid objects/walls
Advantages of 5GHz Frequency Band:
- much faster when communicating over a short distance
- more non-overlapping channels - less chance of interference from other devices
7 of 26
Client-Server Networks
- managed by by a server - the devices connected to the server are clients
- files and software are stored centrally on the server (rather than on individual client devices)
- clients send requests to the server (e.g. asking for data), the server process the request and responds - this is the client-server relationship
- the server stores user profiles, passwords, and access information - it may request a password before fulfilling certain requests or it may deny requests to users without the right access level
- much of the Internet utilises the client-server relationship (e.g. websites are hosted on web servers - web browsers are client programs which send requests to web servers - web servers fulfill requests for thousands of clients
8 of 26
Pros and Cons of Client-Server Networks
Pros:
- easier to manage files as they are stored centrally
- easier to perform back-ups
- easier to install/update software
- easier to manage network security (e.g. anti-malware software and user access levels)
- servers are very reliable and are always on
Cons:
- expensive to set up and needs IT specialists to maintain the network and server
- server dependence - if the server goes down, all clients lose access to their work
- the server may become overloaded if too many clients are accessing it at once
9 of 26
Peer-to-Peer (P2P) Networks (+ Pros and Cons)
- All devices on the network are equal, connecting directly to each other (without a server)
- Files are stored on individual devices (they can then be shared with others)
- May be used at home to share files between devices, or connect devices to a printer
- Used on the Internet for video calling (e.g. Skype) and file sharing
Pros:
- easy to maintain (does not need experience or expertise)
- no dependence on server - if one device fails the whole network is not lost
Cons:
- no centralised management - devices need their updates and security installed individually
- backups are more complicated
- copying files between devices creates duplicate files - making it harder to keep track of what's stored where and which files are up-to-date
- peer machines are less reliable and data may be lost if one of them fails
- machines are prone to slow down when other devices access them
10 of 26
Star Topology

11 of 26
Star Topology Description (+ Pros and Cons)
- All devices are connected to a central switch or server that controls the network
- The central switch allows many devices to access the server simultaneously
- They may be wired or wireless
Pros:
- if one device fails or a cable is disconnected, the rest of the network is unaffected
- easy to add more devices to the network
- better performance than other setups - data goes straight to the central device (switch) so all devices can transmit data at once and there are few data collisions
Cons:
- if the star network is wired, every device will need a cable to connect to central switch or server - this can end up being very expensive
- if there is a problem with the switch or the server, the whole network is affected
12 of 26
Mesh Topology
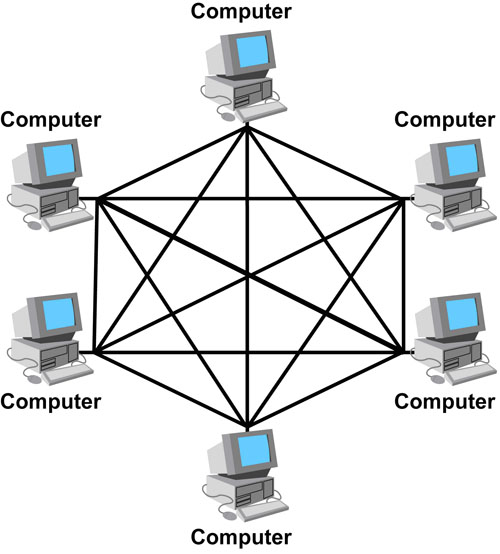
13 of 26
Mesh Topology Description (+ Pros and Cons)
- Mesh networks are decentralised - networking devices are either directly or indirectly connected every other device without the need for a central switch or server
- They work by sending data along the fastest route from one device to another
Pros:
- data can be transmitted from different devices simultaneously
- if one component of the network fails, there is always an alternative route for the data
- can handle high volumes of data traffic
- adding more devices does not increase interference, as all nodes help to transmit data
Cons:
- wired mesh networks are very expensive (as a lot of cabling is required) - however wireless mesh networks do not have this issue
- they require continuous supervision - this makes them hard to manage
14 of 26
Protocols
- A protocol is a set of rules for how devices communicate and how data is transmitted across a network
- Protocols cover how communication between two devices should start and end, how the data should be organised and what the devices should do if data goes missing
15 of 26
Addresses in Networks
MAC Addresses (Media Access Control Address):
- MAC addresses are assigned to all network-enabled devices by the manufacturer
- They are unique to the device and cannot be changed
- They are 48-bit or 64-bit binary numbers (a string of 48 or 64 binary digits or 0s and 1s)
- They are converted into hexadecimal to make them easier to use
- LAN switches read the MAC addresses to send data to the right device
- They are mainly used by the Ethernet protocol on LANs (communication on the same network)
IP Addresses (Internet Protocol Addresses):
- Used to send data between TCP/IP networks (such as over the Internet)
- Are not linked to hardware - they can be assigned either manually (static) or automatically (dynamic) before the device can access the network
- Can either be a 32-bit or 128-bit binary number
- 128-bit numbers are translated into eight hexadecimal numbers
- 32-bit numbers are converted into four denary numbers
16 of 26
Static vs. Dynamic IP Addresses
Static IP Addresses:
- permanent addresses
- used to connect printers on a LAN (as the address for the printer needs to be the same each time, or else it will be too hard to connect to)
- used for hosting websites on the internet (as companies will not want the IP address of their website changing)
- Static IP addresses on the Internet can be very expensive - businesses pay large amounts of money for them
Dynamic IP Addresses:
- assigned when a device logs on to a network, so a device may have a different address each time it connects
- Internet Service Providers (ISPs) often use dynamic IP addresses as they are more cost effective and can be reused
17 of 26
Protocols for Internet-Based Tasks
- HTTP - Hyper Text Transfer Protocol - used by web browsers to access websites and communicate with web servers
- HTTPS - HTTP Secure - more secure version of HTTP, all information sent and received is encrypted
- FTP - File Transfer Protocol - used to access, edit and move files between devices on a network
- POP3 - Post Office Protocol V3 - used to retrieve emails from a server - the server holds the email until you download it, at which point it is deleted from the server
- IMAP - Internet Message Access Protocol - used to retrieve emails from a server - the server holds the email until you delete it (you only download a copy) - used by most web-based email clients
- SMTP - Simple Mail Transfer Protocol - used to send emails and transfer emails between servers
18 of 26
Domain Name Systems
- Every web server has an IP address (e.g 255.255.224.0) which can be entered into the web browserto access the website that it holds
- However, IP addresses are hard to remember as they are made up of a long chain of numbers
- Instead, domain names (e.g. google.com) are used, these are much more user friendly
- The Domain Name System translates between IP address and domain names
- The system consists of DNSs (Domain Name Servers) which store databases of IP address and their corresponding domain names
- Domain Name Servers operate using the client/server relationship:
- Initially, the web browser is the client, as it sends a request to the DNS server to check if the domain name that has been entered is in its database
- The DNS server then checks its database to see if it has the IP address that corresponds to the domain name that has been entered
- If the DNS server doesn't have the IP address, it then becomes the client and sends requests to other DNS servers to find it
- When a DNS server finds the corresponding IP address, it is returned to the original client, so that the user can connect to the website
19 of 26
Connecting to the Internet
- The Internet is the worldwide collection of networks that use the TCP/IP protocol stack
- The World Wide Web (WWW) is the collection of web pages hosted on web servers (it runs using HTTP - Hyper Text Transfer Protocol)
- Internet = Hardware
- Web = Resources hosted on the Internet
- URLs are addresses used to access web servers and the the resources on them:
- e.g. http://getrevising.co.uk/revision-cards/computer-networks
- standard form = protocol://domainname/specific-file-or-page
- Routers:
- transmit data between networks
- used on the Internet to direct data (in packets) to the correct destination
- The Internet uses PACKET SWITCHING to send data between networks
20 of 26
Sending Data Over the Internet - Packets
- An IP address uniquely identifies a device on a network and defines where it is geographically
- The router uses the destination IP address of the packet to identify where it must be sent to, and routing algorithms determine the best route to get the packet there
- Data sent between networks (e.g. on the Internet) is split into equal-sized packets
- There is no fixed path for the packets to take, each packet can take a different route between the sending and the receiving devices
- Each packet consists of 3 components: the header, the payload (data) and the checksum
- The header conatins the control information, which is in 3 parts:
- the destination address (IP and MAC address of where the packet is being sent to)
- the source address (IP and MAC address of where the packet is being sent from)
- the packet number (where the packet is in the sequence of packets)
- The payload is the reason why the data is sent in the first place, it contains the data that the receiver is likely to read (e.g. an email, document etc.)
- The checksum number is a form of validation which ensures that the data has not been corrupted during transmit. The sending and receiving devices calculate a checksum value by performing a function on the payload data - if the values match, the data has been received correctly
21 of 26
Packet Switching
Packet swicthing is used by routers to direct packets on the Internet and other IP networks:
- 1) The sending device splits the data into packets to be sent across the network
- Each packet is given a packet number which corresponds to its place in the sequence of packets
- 2) Each router reads the packet header (for the destination address) and determines which route to send the packet next (according to IP rules)
- 3) The way that the data is sent changes depending on network traffic, so packets take different routes
- If a router receives too many packets at once, it may prioritise some over others
- 4) As the packets take different routes, they can arrive in the wrong order
- The receiving device uses the packet numbers to reassemble them in the right order
- 5) Some packets go missing in transit, so the receiving device periodically checks that all packets have been received - if they haven't it sends a timeout message back to the sending device
- 6) If all data is received and the checksums match, a receipt confirmation is sent to the sending device
- Packet switching is an efficient use of the network, as there as so many possible routes that the packets can take, so data can be sent even if there is heavy traffic
22 of 26
The Cloud
- Cloud computing is the delivery of services over the cloud (the Internet)
- Data is hosted (stored) by the cloud provider, and accessed by the client
- Cloud computing is like an extension of a tradional client-server network - files are hosted by a business, which acts as the server
Pros:
- Services can be accessed from any connected device
- Hardware is managed externally (covers cost and expertise)
- Cloud software will be updated automatically
- Host provides better security and back-ups
Cons:
- Connection to the Internet needed to access files
- Full reliance on host
- Data in the cloud can be vulnerable to hackers
- Subscription fees for cloud storage and software may be expensive (especially for smaller users)
23 of 26
Virtual Networks
- entirely software-based
- created by sectioning off some of a physical network's bandwidth
- several virtual networks can exist on the same physical network - these networks all share the same hardware, making them more efficient than standard physical networks
- each virtual network can have its own security (including its own firewall) - this means that they can only be accessed by using certain software or login credentials
- a Virtual Private Network (VPN) is a type of virtual networks that can beused to send data securely over a large network (e.g. a WAN or the Internet)
- e.g. a VPN can be used to send data securely between two offices on different sites, or to set up a school intranet that all students can access from home
- a Virtual LAN allows you to split a LAN into several separate networks using the same hardware
24 of 26
Layers
Advantages of using layers:
- they break the process down into manageable parts (decomposition)
- they are self-contained - they can be changed without other layers being affected
- having set rules for each layer forces companies to make compatible, universal hardware and software, so different brands will work with each other and work in the same way
- LAYER 1 - LINK LAYER - passing data over the physical network, responsible for how bits are sent as electrical signals over cables, wireless and other hardware - uses Ethernet protocol
- LAYER 2 - NETWORK LAYER - making connections between networks, directing data packets and handling traffic + used by routers - uses IP protocol
- LAYER 3 - TRANSPORT LAYER - controlling data flow, splitting data into packets and checking packets are correctly sent and delivered - uses TCP protocol
- LAYER 4 - APPLICATION LAYER - operating network applications, such as web browsers and email clients - uses HTTP(S), FTP, SMTP, POP3, IMAP protocols
SENDING DATA GOES FROM THE APPLICATION LAYER TO THE LINK LAYER
RECEIVING DATA GOES FROM THE LINK LAYER TO THE APPLICATION LAYER
25 of 26
TCP/IP Protocols
TCP (Transmission Control Protocol):
- operates at transport layer
- deals with the connection between devices
- covers splitting data into packets and reassembling the packets back into the original data once they reach the receiving device
- checks that data is correctly sent and delivered
- sends acknowledgement to sender when data is received - if the data is not received a timeout message is sent, so that the data is re-sent
IP (Internet Protocol):
- operates at network layer
- responsible for packet switching
- addresses packets withthe source and destination IP address
- removes IP addresses when they are no longer needed
26 of 26
Related discussions on The Student Room
- It service delivery »
- careers »
- What jobs can I get since I got a 2:2 and this degree »
- GCSE Computer Science - Struggling with Networks »
- Please I need help on how to rearrange these blockchain »
- Can computer science degree course accept BTECH applied science students »
- Anyone been or going university of metropolitan? »
- Unit 14 IT Service Delivery Part A Question »
- Equipment needed for Computing course? »
- Computer Communications and Networks »
Similar Computing resources:
0.0 / 5
0.0 / 5
0.0 / 5
0.0 / 5
0.0 / 5
3.0 / 5 based on 2 ratings
5.0 / 5 based on 1 rating
Teacher recommended
0.0 / 5
0.0 / 5
0.0 / 5


Comments
Report
Report
Report